How to Set Up SSH Keys Between Servers
SSH Keys
SSH keys serve as a means of identifying yourself to an SSH server using public-key cryptography and challenge-response authentication. One immediate advantage this method has over traditional password authentication is that you can be authenticated by the server without ever having to send your password over the network. Anyone eavesdropping on your connection will not be able to intercept and crack your password because it is never actually transmitted. Additionally, using SSH keys for authentication virtually eliminates the risk posed by brute-force password attacks by drastically reducing the chances of the attacker correctly guessing the proper credentials.
How SSH Keys work?
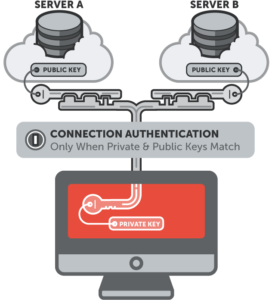
SSH Keys are always 2, which are Private and Public key. The Private key stays in the client system and must be well protected, getting into the wrong hands can grant access to the server which you sent your public key to. While the Public key is sent to the server which whenever a connection is made to the server, it composes a message and sends a challenge to the requesting client. This challenge message must be solved by the private key of the requesting client to grant access.
Generating Keys
These keys an be generated with ssh-keygen command by typing:
$ ssh-keygen
Generating public/private rsa key pair. Enter file in which to save the key (/home/donjajo/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/donjajo/.ssh/id_rsa. Your public key has been saved in /home/donjajo/.ssh/id_rsa.pub. The key fingerprint is: SHA256:6O8/+UCmr3nnJH0Q+Px+kvbtTXvQF62J4N7URcl3mrQ [email protected] The key's randomart image is: +---[RSA 2048]----+ | . .| | . .o+| | . .. =+| | . .o .E.o| | . S.o.+o =.| | . +..oo= o| | . ..o+o ooo| | . o=+oo+.*| | .=+o=o..**| +----[SHA256]-----+
This key is saved in your ~/.ssh which is your home directory.
Setting Up SSH Keys
To setup these keys to start working, we will need to copy the public key to the server and authorize it. Then we make the private key private to the owner. The keys saved to ~/.ssh/, we will copy id_rsa.pub to the server using scp
$ scp ~/.ssh/id_rsa.pub user@server_addr:~/
We copied the id_rsa.pub to the home directory, now we are to login to the server and authorize the key.
$ ssh user@server_addr
Enter password and login, we will create the directory ~/.ssh if not exist
$ mkdir ~/.ssh
Append contents of the ~/id_rsa.pub to ~/.ssh/authorized_keys
$ cat ~/id_rsa.pub >> ~/.ssh/authorized_keys
Lock down ~/.ssh/authorized_keys to the owner
$ chmod 600 ~/.ssh/authorized_keys
Logout of the server, back to the client and lock down the private key to the owner
$ chmod 600 ~/.ssh/id_rsa
Testing your Setup
With everything done, logging in shouldn’t ask for password anymore. If this is successful, you can disable password login entirely from the server, by editing /etc/ssh/sshd_config find:
#PasswordAuthentication yes
And change to
PasswordAuthentication no
Restart sshd
Hope this helps…