Spoof HTTP Headers Using Squid Proxy Server
What are HTTP Headers?
HTTP headers are the core part of these HTTP requests and responses, and they carry information about the client browser, the requested page, the server and more.
Examples of HTTP Headers
What your browser sends to the server:
|
1 2 3 4 5 6 7 8 |
GET / HTTP/1.1 Host: donjajo.com User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Cookie: __cfduid=dedb7c82f; Connection: keep-alive |
This interprets, my browser requests for the directory / on the host donjajo.com using the User-Agent of my browser and other provided data. Now the Server will reply:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
HTTP/2.0 200 OK Date: Sat, 27 Aug 2016 19:23:57 GMT Content-Type: text/html; charset=UTF-8 Expires: Wed, 11 Jan 1984 05:00:00 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Link: <https://donjajo.com/wp-json/>; rel="https://api.w.org/", <https://wp.me/50p14>; rel=shortlink Server: cloudflare-nginx CF-RAY: 2d91e696ff7c35b4-LHR Content-Encoding: gzip X-Firefox-Spdy: h2 <!DOCTYPE html> <html lang="en-US" xmlns:fb="http://ogp.me/ns/fb#" xmlns:addthis="http://www.addthis.com/help/api-spec" prefix="og: http://ogp.me/ns#"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1"> <link rel="pingback" href="https://donjajo.com/xmlrpc.php"> <!--[if lt IE 9]><script src="https://donjajo.com/wp-content/themes/wpex-mesa/js/html5.js"></script><![endif]--> <link rel="profile" href="http://gmpg.org/xfn/11"> <title>Don Jajo - It's me, it's my blog...</title> [...] |
These headers determines what you get from the server as the browser requests, a developer can reference any of the headers sent from the client (browser) and can return something based on what is in the header.
Spoofing HTTP Headers
These headers can be spoofed too, they are couple of browser add-ons to do this. But in this post I will be showing you how to do this with Squid Proxy in Linux
Squid Proxy Server
Squid offers a rich access control, authorization and logging environment to develop web proxy and content serving applications. Squid offers a rich set of traffic optimization options, most of which are enabled by default for simpler installation and high performance.
With these, Squid can manipulate most HTTP Requests and Response passed through it.
Installing Squid Proxy Server
If you don’t have it installed, install it using:
$ sudo apt install squid
Some distribution uses squid3
Configuring Squid Proxy Server
Firstly, we have to tell Squid Proxy to really serve as HTTP proxy server and accept requests from HTTP because by default this is disabled. We will have to edit the config file located at /etc/squid/squid.conf and find the line
# And finally deny all other access to this proxy http_access deny all
Change it to
# And finally deny all other access to this proxy http_access allow all
Then save and reload Squid with $ sudo systemctl restart squid
With what we are about to do – to spoof HTTP Headers is regarded as violating HTTP Rules, this is not enabled by default in most Linux Distribution. We have to tell Squid to neglect HTTP rules and violate it, to check if this option is enabled run this:
$ sudo squid -v | grep violations --color
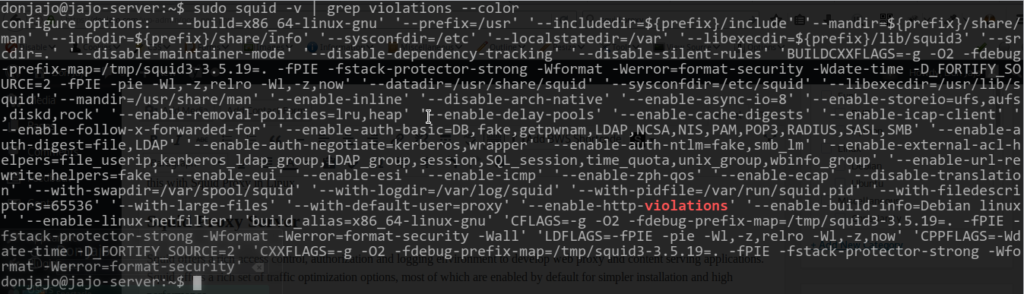 If you see something similar to the above image, then it is enabled and can allow spoofing of HTTP Headers. Else if it returns nothing means it is not enabled and you need to rebuild the package to enable it.
If you see something similar to the above image, then it is enabled and can allow spoofing of HTTP Headers. Else if it returns nothing means it is not enabled and you need to rebuild the package to enable it.
Enabling an Option in Squid Proxy
If your output is similar to the above image, you can skip this step. Else you can proceed.
I made a post on how to Rebuild package in Debian/Ubuntu, from the post; after downloading source files and build dependencies, don’t rebuild yet. Edit in the Squid source files directory debian/rules like assuming the source files are in /tmp/squid3-3.5.19/ you are to edit the file /tmp/squid3-3.5.19/debian/rules. You should find something similar to this:
DEB_CONFIGURE_EXTRA_FLAGS := BUILDCXXFLAGS="$(CXXFLAGS) $(CPPFLAGS) $(LDFLAGS)" \ --datadir=/usr/share/squid \ --sysconfdir=/etc/squid \ --libexecdir=/usr/lib/squid \ --mandir=/usr/share/man \ --enable-inline \ --disable-arch-native \ --enable-async-io=8 \ --enable-storeio="ufs,aufs,diskd,rock" \ --enable-removal-policies="lru,heap" \ --enable-delay-pools \ --enable-cache-digests \ --enable-icap-client \ --enable-follow-x-forwarded-for \ --enable-auth-basic="DB,fake,getpwnam,LDAP,NCSA,NIS,PAM,POP3,RADIUS,SASL,SMB" \ --enable-auth-digest="file,LDAP" \ --enable-auth-negotiate="kerberos,wrapper" \ --enable-auth-ntlm="fake,smb_lm" \ --enable-external-acl-helpers="file_userip,kerberos_ldap_group,LDAP_group,session,SQL_session,time_quota,$ --enable-url-rewrite-helpers="fake" \ --enable-eui \ --enable-esi \ --enable-icmp \ --enable-zph-qos \ --enable-ecap \ --disable-translation \ --with-swapdir=/var/spool/squid \ --with-logdir=/var/log/squid \ --with-pidfile=/var/run/squid.pid \ --with-filedescriptors=65536 \ --with-large-files \ --with-default-user=proxy
These are list of options enabled by default, then all you have to do it goto the end and add yours, which will be --enable-http-violations making it look like
[...]--with-large-files \ --with-default-user=proxy \ --enable-http-violations
Save the file and go back to this post
Spoofing Request Headers
Now we have Squid built with --enable-http-violations enabled, lets go ahead and spoof request headers. Making sure Squid is working, we will run a command:
$ curl -I http://donjajo.com --proxy http://127.0.0.1:3128 HTTP/1.1 301 Moved Permanently Date: Sat, 27 Aug 2016 20:42:50 GMT Content-Type: text/html; charset=iso-8859-1 Set-Cookie: __cfduid=dfdcd26b61d2d280e0e31732101196b051472330570; expires=Sun, 27-Aug-17 20:42:50 GMT; path=/; domain=.donjajo.com; HttpOnly Location: https://donjajo.com/ ngpass_ngall: 1 Server: MyOwn/1.1 CF-RAY: 2d925a33480334dc-LHR X-Cache: MISS from jajo-server X-Cache-Lookup: MISS from jajo-server:3128 Via: 1.1 jajo-server (squid/3.5.19) Connection: keep-alive
We could spot 1.1 jajo-server (squid/3.5.19) in the response, means our Squid is working! 🙂
Now we are going to spoof the sent request, lets change our User-Agent and Referer to something else. Edit the config file again /etc/squid/squid.conf and goto the last line and add these
#Block a header value from being sent to server request_header_access User-Agent deny all request_header_access Referer deny all #Modify them request_header_replace User-Agent NewUserAgent/1.1 request_header_replace Referer donjajo.com
request_header_access directive allows our blocks a value in HTTP sent request, we used it above to block
request_header_replace directive is use to replace blocked HTTP Header value, as we used it to replace User-Agent and Referer
Restart Squid and set your browser Proxy to 127.0.0.1:3128 and check your headers
Spoofing Response Header
As request headers can be spoofed, so is response headers. Using same method as above but with reply_header_access and reply_header_replace
We can replace the Server Signature sent from the server to something else by adding:
reply_header_access Server deny all reply_header_replace Server MyOwn/1.1
Save and restart Squid, your response should be what you set.
Adding Header Parameter
As we can modify these headers, we can as well add our custom header. This is easily done by adding this line
#For Request request_header_add Author Jajo #For Response (This directive is not available in Squid 3.5.x) reply_header_add CustomValue true
Save and don’t forget to restart Squid.
Summary
Wit this, we have gotten to know how to use Squid Proxy to spoof HTTP Headers. Squid has many features as its robust, this is just the tip of an iceberg from Squid.